#Encrypted Device Data Recovery
Explore tagged Tumblr posts
Text
LaCie Rugged SSD and SSD Pro Storage Solutions - Videoguys
New Post has been published on https://thedigitalinsider.com/lacie-rugged-ssd-and-ssd-pro-storage-solutions-videoguys/
LaCie Rugged SSD and SSD Pro Storage Solutions - Videoguys


Built to roam, built to play. Our durable lineup of Rugged NVMe SSDs are ready to explore. Built forward-compatible up to USB 40Gbps and Thunderbolt 4, these rugged drives are engineered to handle a broad range of creative production demands. Vloggers, videographers, freelancers, indie filmmakers, even weekend warriors—we’ve got you covered
Transfer and edit RAW 4K video with speeds of up to 1050MB/s
USB Type-C interface is universally compatible
Enjoy extreme ruggedness with an IP67 waterproof rating
Trek anywhere with 3-meter drop and two-ton car crush resistance
Protect projects with Seagate Secure encrypted USB drive technology
5-year Rescue Data Recovery Services

Level Up Your 4K Video ProjectGive your workflow a substantial boost with Rugged SSD. With speeds 2× faster than traditional SATA SSDs, this encrypted USB drive uses Seagate FireCuda NVMe SSD performance to maximize USB 3.1 Gen 2 throughput while delivering IP67 waterproof strengt
Sprint ahead with Thunderbolt 3 SSD speeds of up to 2800MB/s
Use it seamlessly with USB 3.1 Gen 2 devices
Enjoy extreme ruggedness with an IP67 waterproof rating
Trek anywhere with 3-meter drop and two-ton car crush resistance
5-year Rescue Data Recovery Services

Harness 6K Video and Beyond Rugged SSD Pro fuses the blazing-fast Seagate FireCuda NVMe SSD with a Thunderbolt 3 interface, unleashing speeds 5× faster than traditional SATA SSDs so that you can play back and render the most demanding high bit rate RAW content—like 6K, 8K, and super slo-mo source files.
Rugged SSD
Rugged SSD Pro
Special Features
Hardware encryption, ultra small & extreme ruggedness
Ultra-fast and small, extreme ruggedness
Storage Type
Max Speeds
Works With
USB 40Gbps
USB 20Gbps
USB10Gbps
USB5Gbps
ThunderboltTM 4
ThunderboltTM 3
USB 40Gbps
USB 20Gbps
USB10Gbps
USB5Gbps
ThunderboltTM 4
ThunderboltTM 3
Drop Resistance
Crush Resistance
Environmental Resistance
IP67 rated: water/dust
IP67 rated: water/dust
Hardware Encryption
Incl. Cables & Adapters
USB-C (USB 3.1 10GB/s)
Thunderbolt 3
Limited Warranty
Data Recovery Services
#4K#8K#amp#cables#content#data#data recovery#devices#dust#encryption#Environmental#Features#freelancers#Hardware#it#max#performance#Play#Production#recovery#Rescue#sprint#Storage#technology#transfer#usb#USB-C#Video#water#workflow
0 notes
Text
For those who are not aware: Bitlocker is encryption software, it encrypts your computer and makes it impossible to access the information on the computer unless you have the key.
It should be standard practice for IT companies to document the bitlocker keys as they are configuring bitlocker on a computer; generally you would do this by creating a record in your client management software for that specific device and putting the key in the record. Sometimes software can be used to extract that information in the event that it's necessary, but even if there's theoretically a way to extract the key, it should be documented somewhere *other* than on the encrypted computer.
This is something that a lot of IT people fuck up on kind of a lot (we've definitely had problems with missing bitlocker keys and I'm quite happy that the people who didn't document those keys aren't my coworkers anymore).
So what do you do if you want to use encryption software and you're NOT an IT company using a remote management tool that might be able to snag the keys?
When you are setting up encryption, put the encryption key in your password manager. Put it in your password manager. Document the important information that you cannot lose in your password manager. Your password manager is a good place to keep important things like your device encryption key, which you do not want lost or stolen. (If you run your password manager locally on an encrypted computer, export the data every once in a while, save it as an encrypted file, and put the file on your backup drive; you are going to have a bad time if your computer that hosts the only copies of your passwords shits the bed so *make a backup*)
This is my tip for home users for any kind of important recovery codes or software product keys: Print out the key and put it in your underwear drawer. Keep it there with your backup drive. That way you've got your important (small) computer shit in one place that is NOT your computer and is not likely to get shifted around and lost (the way that papers in desks often get shifted around and lost).
2K notes
·
View notes
Text
Hi yes I would like to start down this rabbit hole please because I'm totally normal about this ... I am convinced Jon and Martin are part of a tape drive. It links with the tapes from TMA and the trailer for TMP especially with the opening computer screen (I already posted about my thoughts on that).
What is a tape drive?
A tape drive is a device that stores computer data on magnetic tape, especially for backup and archiving purposes. Like an ordinary tape recorder, a tape drive records data on a loop of flexible celluloidlike material that can be read and also erased.
Tape drives differ from hard disk drives (HDDs) and solid-state drives (SSDs) in the way data is read and written to the storage media. Tapes store data sequentially, whereas HDDs and SSDs use rotating disks with rapidly moving seek heads, nonmoving flash memory or similar technology to transfer data.
Drives come in many sizes and capabilities. They are sold as standalone units or stacked in data center racks, creating tape libraries. The tapes themselves are often housed in sealed cassettes that can be inserted into the drive and activated.
There are several benefits to using tape drives, particularly for backup and archival uses. They include the following:
Capacity. Tapes have a large capacity for storing data when compared to HDDs.
Low cost. They are economical when compared to other storage media.
Life span. Tapes stored in a suitable environment can last for decades, an important factor for archival storage.
Transportable. Tapes can be easily moved from one location to another and are considered off-line storage.
Disaster recovery. Tape is often the storage medium of choice for data backup and DR. Storing critical systems and data on tape creates an air gap between systems that are at risk from cyber attacks simply by removing the tape cassette from the drive.
Security. Today, tapes support encryption such as Advanced Encryption Standard-256 and provide varying levels of data protection.



#the magnus archives#martin blackwood#jonathan sims#tma#jonmartin#the magnus protocol#magnus pod#tmp#tmp theory#jon sims#jmart#jonny sims#tape drive#tapes!#jmart is in the tapes!
190 notes
·
View notes
Text
v1.2 "Nautilus" is live!

This release further polishes the Octocon app's user experience and adds a bunch of new features, including polls, end-to-end encryption for journal entries, and locks for custom fields and journal entries!
Keep reading to see a quick highlight of this version's changes!
Features
🗳️ Polls
Polls are a new feature that allows your alters to vote on important decisions!
Two poll types are currently available: "vote" and "choice." Vote polls let alters vote between "Yes," "No", "Abstain," and (optionally) "Veto," while choice polls let you make your own choices!
Access polls by opening the navigation drawer with the button in the top-left or by swiping right anywhere in the app.
🔐 End-to-end encryption
We take the security of your data extremely seriously, which is why we're proud to announce that Octocon now uses end-to-end encryption to lock down your journal entries!
Next time you attempt to journal, you'll be prompted to set up encryption, and will be given a recovery code.
Write this code down somewhere safe, like a physical piece of paper! You'll need it to if you uninstall the app or log in on another device.
Once set up, all journal entries you write will be encrypted on your device before being sent to our servers. This makes it literally impossible for both the Octocon team (and hackers, in the case of a data breach) to look at your data.
All previously written journal entries will not be encrypted, but you can encrypt them by simply making a small change and saving them again.
This doesn't necessarily mean that your journal entries were unsafe before! We make every effort to keep our servers secure and our team never looks at user data; this is just a safeguard to make your sensitive data essentially bulletproof.
Please note that - by design - if you lose your recovery code after setting up encryption, it is impossible for us to recover your data! You'll have to start all over again.
🔒 Journal entry & custom field locks
Journal entries and custom fields can now be "locked," ensuring that you can't view them accidentally if you're not in the right headspace!
Upon being locked, journal entries will force you to tap a button three times to confirm that you'd like to open it.
Similarly, locked custom fields will be blurred until tapping them three times.
Other
A new onboarding screen has been added to help new users understand the app's functionality and point them towards our community.
All links in the app are now opened using Android's "custom tabs" API. No more jank caused by opening links in a separate browser!
Journal entries can now be "pinned" to keep them at the top of the list.
A new mode to change front (swiping further left on an alter to set as main front instead of swiping right).
You can keep the old functionality by using the "Swipe (Bidirectional)" change front mode instead!
Changes
Alters and tags now have their UI split into tabs to more easily sift through information.
Complex alter data (like descriptions and custom fields) is now loaded lazily to reduce the app's initial loading time and bandwidth usage, especially for larger systems.
Various elements of the UI have been reworked, especially regarding effective use of color.
The settings screen has been organized into multiple separate screens.
The bottom navigation bar now collapses when scrolling down (this can be disabled in the settings).
Fixes
The app should no longer crash in the case of a temporary network outage, or upon startup if you have no connection at all.
Friend data is now kept in a cache while navigating through their profile, which greatly reduces the amount of loading screens.
This is just a highlight of the many changes this update brings! You can view a full changelog in our official Discord server.
#Octocon#Octocon update#Octocon app#Octocon bot#system#did system#osdd system#did#osdd#osddid#did osdd
14 notes
·
View notes
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Text
How To Reduce 5G Cybersecurity Risks Surface Vulnerabilities

5G Cybersecurity Risks
There are new 5G Cybersecurity Risks technology. Because each 5G device has the potential to be a gateway for unauthorized access if it is not adequately protected, the vast network of connected devices provides additional entry points for hackers and increases the attack surface of an enterprise. Network slicing, which divides a single physical 5G network into many virtual networks, is also a security risk since security lapses in one slice might result in breaches in other slices.
Employing safe 5G Cybersecurity Risks enabled devices with robust security features like multi-factor authentication, end-to-end encryption, frequent security audits, firewall protection, and biometric access restrictions may help organizations reduce these threats. Regular security audits may also assist in spotting any network vulnerabilities and taking proactive measures to fix them.
Lastly, it’s preferable to deal with reputable 5G service providers that put security first.
Take On New Cybersecurity Threats
Cybercriminals often aim their biggest intrusions at PCs. Learn the characteristics of trustworthy devices and improve your cybersecurity plan. In the current digital environment, there is reason for worry over the growing complexity and frequency of cyber attacks. Cybercriminals are seriously harming businesses’ reputations and finances by breaking into security systems using sophisticated tools and tactics. Being able to recognize and address these new issues is critical for both users and businesses.
Threats Driven by GenAI
Malicious actors find it simpler to produce material that resembles other individuals or entities more authentically with generative AI. Because of this, it may be used to trick individuals or groups into doing harmful things like handing over login information or even sending money.
Here are two instances of these attacks:
Sophisticated phishing: Emails and other communications may sound much more human since GenAI can combine a large quantity of data, which increases their credibility.
Deepfake: With the use of online speech samples, GenAI is able to produce audio and maybe even video files that are flawless replicas of the original speaker. These kinds of files have been used, among other things, to coerce people into doing harmful things like sending money to online fraudsters.
The mitigation approach should concentrate on making sure that sound cybersecurity practices, such as minimizing the attack surface, detection and response methods, and recovery, are in place, along with thorough staff training and continual education, even if both threats are meant to be challenging to discover. Individuals must be the last line of defense as they are the targeted targets.
Apart from these two, new hazards that GenAI models themselves encounter include prompt injection, manipulation of results, and model theft. Although certain hazards are worth a separate discussion, the general approach is very much the same as safeguarding any other important task. Utilizing Zero Trust principles, lowering the attack surface, protecting data, and upholding an incident recovery strategy have to be the major priorities.Image Credit To Dell
Ransomware as a Service (RaaS)
Ransomware as a Service (RaaS) lets attackers rent ransomware tools and equipment or pay someone to attack via its subscription-based architecture. This marks a departure from typical ransomware assaults. Because of this professional approach, fraudsters now have a reduced entrance barrier and can carry out complex assaults even with less technical expertise. There has been a notable rise in the number and effect of RaaS events in recent times, as shown by many high-profile occurrences.
Businesses are encouraged to strengthen their ransomware attack defenses in order to counter this threat:
Hardware-assisted security and Zero Trust concepts, such as network segmentation and identity management, may help to reduce the attack surface.
Update and patch systems and software on a regular basis.
Continue to follow a thorough incident recovery strategy.
Put in place strong data protection measures
IoT vulnerabilities
Insufficient security makes IoT devices susceptible to data breaches and illicit access. The potential of distributed denial-of-service (DDoS) attacks is increased by the large number of networked devices, and poorly managed device identification and authentication may also result in unauthorized control. Renowned cybersecurity researcher Theresa Payton has even conjured up scenarios in which hackers may use Internet of Things (IoT) devices to target smart buildings, perhaps “creating hazmat scenarios, locking people in buildings and holding people for ransom.”
Frequent software upgrades are lacking in many IoT devices, which exposes them. Furthermore, the deployment of more comprehensive security measures may be hindered by their low computational capacity.
Several defensive measures, such assuring safe setup and frequent updates and implementing IoT-specific security protocols, may be put into place to mitigate these problems. These protocols include enforcing secure boot to guarantee that devices only run trusted software, utilizing network segmentation to separate IoT devices from other areas of the network, implementing end-to-end encryption to protect data transmission, and using device authentication to confirm the identity of connected devices.
Furthermore, Zero Trust principles are essential for Internet of Things devices since they will continuously authenticate each user and device, lowering the possibility of security breaches and unwanted access.
Overarching Techniques for Fighting Cybersecurity Risks
Regardless of the threat type, businesses may strengthen their security posture by taking proactive measures, even while there are unique tactics designed to counter certain threats.
Since they provide people the skills and information they need to tackle cybersecurity risks, training and education are essential. Frequent cybersecurity awareness training sessions are crucial for fostering these abilities. Different delivery modalities, such as interactive simulations, online courses, and workshops, each have their own advantages. It’s critical to maintain training sessions interesting and current while also customizing the material to fit the various positions within the company to guarantee its efficacy.
Read more on govindhtech.com
#Reduce5G#CybersecurityRisks#5Gservice#ZeroTrust#generativeAI#cybersecurity#strongdata#onlinecourses#SurfaceVulnerabilities#GenAImodels#databreaches#OverarchingTechniques#technology#CybersecurityThreats#technews#news#govindhtech
2 notes
·
View notes
Text
Synology Data Recovery: A Comprehensive Guide
Synology is renowned for its NAS (Network Attached Storage) devices, which offer robust data storage solutions for both personal and business use. Despite their reliability and advanced features, data loss can still occur due to various reasons. This guide provides a comprehensive overview of Synology data recovery, covering the causes of data loss, the steps to recover lost data, and best practices to safeguard your data.
Understanding Synology NAS
Synology NAS devices are designed to provide a centralized and accessible storage solution with features such as RAID (Redundant Array of Independent Disks) configurations, data protection, and easy-to-use interfaces. They support multiple users and applications, making them a versatile choice for data storage and management.
Common Causes of Data Loss
Data loss in Synology NAS devices can result from various scenarios, including:
1. Hardware Failures
Disk Failure: Hard drives can fail due to age, physical damage, or manufacturing defects.
Power Surges: Electrical surges can damage the Synology NAS’s internal components.
Overheating: Inadequate cooling can lead to overheating, causing hardware malfunctions.
2. Software Issues
Firmware Corruption: Problems during firmware updates or bugs can lead to data corruption.
File System Errors: Corrupt file systems can make data inaccessible.
3. Human Error
Accidental Deletion: Users can mistakenly delete important files or entire volumes.
Misconfiguration: Incorrect setup or configuration changes can lead to data loss.
4. Malicious Attacks
Ransomware: Malware can encrypt data, making it inaccessible until a ransom is paid.
Viruses: Malicious software can corrupt or delete data.
Steps for Synology Data Recovery
When faced with data loss on a Synology NAS device, it’s crucial to follow a structured approach to maximize recovery chances. Here are the steps to follow:
1. Stop Using the Device
Immediately stop using the Synology NAS to prevent further data overwriting. Continuing to use the device can reduce the likelihood of successful data recovery.
2. Diagnose the Problem
Identify the cause of the data loss. Understanding whether the issue is due to hardware failure, software problems, human error, or a malicious attack will help determine the best recovery method.
3. Check Backups
Before attempting data recovery, check if there are any recent backups. Regular backups can save time and effort in the recovery process. If backups are available, restore the lost data from them.
4. Use Data Recovery Software
For minor data loss issues, data recovery software can be an effective solution. Several reliable tools support Synology NAS devices:
R-Studio: A powerful tool for recovering data from various storage devices, including Synology NAS.
EaseUS Data Recovery Wizard: User-friendly software that can recover files lost due to deletion, formatting, or system crashes.
Stellar Data Recovery: Known for its robust recovery capabilities, supporting Synology NAS and RAID configurations.
5. Consult Professional Data Recovery Services
For severe data loss scenarios, such as hardware failures or extensive corruption, it is advisable to seek help from professional data recovery services. These experts have the tools and knowledge to recover data from damaged Synology NAS devices. Some reputable data recovery companies include:
DriveSavers Data Recovery: Offers specialized services for Synology and other RAID systems, with a high success rate.
Ontrack Data Recovery: Known for its expertise in NAS and RAID recovery, Ontrack provides comprehensive solutions for Synology devices.
Gillware Data Recovery: Provides professional data recovery services, specializing in complex RAID and NAS systems.
6. Prevent Future Data Loss
After successfully recovering your data, implement measures to prevent future data loss:
Regular Backups: Schedule frequent backups to ensure you have up-to-date copies of your data.
Firmware Updates: Keep your Synology firmware updated to protect against bugs and vulnerabilities.
Surge Protectors: Use surge protectors to safeguard against electrical surges.
Proper Ventilation: Ensure adequate ventilation and cooling to prevent overheating.
Conclusion
Data loss on Synology NAS devices, though distressing, can often be remedied with the right approach. By understanding the common causes of data loss and following a systematic recovery process, you can effectively retrieve lost data. Utilize reliable data recovery software or consult professional services for severe cases. Additionally, implementing preventive measures will help safeguard your data against future loss, ensuring that your Synology NAS device continues to serve as a reliable data storage solution.
2 notes
·
View notes
Text
PHONE HACKER, FOR REMOTELY ACCESSING SMARTPHONES > FOLKWIN EXPERT RECOVERY.
You can be very sure to reach Folkwin Expert Recovery and contact them through this Email: FOLKWINEXPERTRECOVERY { @ } TECH-CENTER { dot } COM Or WhatsApp: +1 {769} - 280 - 0965 Telegram: @Folkwin_expert_recovery. ln a world where technology plays a significant role in our lives, the discovery of infidelity through digital means has become increasingly common. With the emergence of advanced tools and techniques, one such solution that has gained attention is Folkwin Expert Recovery. This article aims to introduce you to the capabilities of Folkwin Expert Recovery and how it claims to expose a cheating spouse by hacking their phone to gain access to messages. A leading-edge program called Folkwin Expert Recovery can assist you in revealing the truth that may be hiding in the shadows of your online life. It's similar to having a Folkwin at your side who is prepared to perform magic and divulge previously unknown information. Using advanced techniques and algorithms, Folkwin Expert Recovery can access and retrieve data from various sources, including smartphones. It delves into the labyrinth of technology, navigating through firewalls and encryption to uncover messages and information that may have been hidden or deleted. Phone hacking might sound like something out of a Hollywood movie, but it's a real phenomenon that has become more prevalent in our digital age. It involves gaining unauthorized access to someone's device to retrieve or manipulate data, such as messages, photos, or call logs. When it comes to choosing a tech team to help you gather evidence of your suspicions, doing your research is crucial. Start by looking into the team's track record and client testimonials. Have they successfully assisted others in similar situations? Do their clients speak highly of their work? Reading reviews and testimonials can give you valuable insights into their reputation and expertise. Certifications and industry recognition are important indicators of a tech team's expertise and professionalism. Look for teams that have relevant certifications and memberships in professional organizations. These credentials demonstrate that they have met certain standards and are committed to staying up-to-date with the latest industry practices. A reputable team will proudly display their certifications and any industry awards they have received. Their proficiency in digital forensics allows them to navigate through complex digital footprints, ensuring no stone is left unturned. Moreover, working with a specialized team like Folkwin Expert Recovery means you're partnering with experts who understand the nuances of relationship investigations. Their experience and knowledge in this specialized field give you an added advantage in gathering the evidence you need. Remember, the journey of uncovering infidelity is not an easy one, but with the right team by your side, you can gain the clarity and evidence you seek. Folkwin Expert Recovery is here to provide an unmatched level of expertise and support to help you through this challenging time. I send my regards, Sophia Taylor.
2 notes
·
View notes
Text
Data Recovery Solutions: Restoring Files After System Failures
In today’s digital landscape, data is more than just a collection of files; it’s essential to both personal and professional life. From important business documents to cherished family photos, losing data can be incredibly frustrating. System failures, whether caused by software corruption, hardware malfunctions, or unexpected power surges, are among the primary reasons data loss occurs. Fortunately, various data recovery solutions can help restore files after such failures. This article explores the most effective ways to recover data after system failures, from simple DIY methods to professional solutions.
1. Understanding System Failures and Their Impact on Data
A system failure occurs when a computer or device encounters an error that prevents it from functioning properly. These failures can occur due to many reasons, such as:
Hardware Failures: Hard drive crashes, damaged cables, or power supply issues can prevent the system from booting up.
Software Failures: Corrupted operating systems, buggy applications, or viruses that compromise system integrity can lead to inaccessible files or system crashes.
Power Surges or Outages: Sudden power cuts or surges can disrupt the normal functioning of hardware, causing data corruption or loss.
Human Error: Accidental file deletion, formatting, or partition loss due to incorrect settings can also cause data loss.
Understanding the nature of the failure is key to determining which recovery approach will work best for your situation.
2. Backup Strategies: The First Line of Defense
While this section is not a direct recovery solution, a solid backup strategy is the best preventive measure against data loss due to system failures. Regular backups help protect your data, making it easier to restore in case of an emergency.
There are several methods to back up your data:
Cloud Storage: Services like Google Drive, Dropbox, and iCloud allow you to store files remotely and access them from any device. These services offer automatic syncing, making it easy to keep your files safe without manual intervention.
External Hard Drives: An external hard drive is a reliable way to create a local backup of your files. It’s important to set up scheduled backups to ensure the most recent data is saved.
Network Attached Storage (NAS): NAS devices are used in larger environments or homes with multiple devices. They provide centralized storage and can be configured for automatic backups of all connected devices.
In the event of system failure, a well-maintained backup can save you from the headache of trying to recover lost data. However, if no backup exists, data recovery becomes necessary.
3. Using Operating System Tools for Recovery
When faced with system failures, sometimes the operating system itself offers built-in tools to help recover lost files or restore the system to working condition.
Windows Recovery Options
Windows has a suite of built-in recovery tools that can be accessed even when the system fails to boot properly.
System Restore: This feature lets you restore the operating system to a previous state before the failure occurred. It doesn’t affect your personal files but will remove any software or updates installed after the restore point.
Startup Repair: If Windows fails to boot, this tool can help fix issues related to corrupted system files or startup configuration.
CHKDSK: If your system’s hard drive has file system issues, running the chkdsk command from the Command Prompt can identify and fix minor errors without overwriting data.
macOS Recovery Options
For macOS users, Apple offers several tools to restore files or recover the system after failure.
Time Machine: If you have been using Time Machine for backups, it’s an excellent way to restore your system to a previous state. Simply launch Time Machine and select the backup you wish to restore.
macOS Recovery: In cases of OS corruption or other issues, macOS Recovery provides tools like "Disk Utility" to repair the disk or reinstall macOS without erasing your files.
These built-in tools are often sufficient for minor system issues, but they may not work for severe failures or physical damage to hardware.
4. Third-Party Data Recovery Software
If built-in recovery tools fail, third-party data recovery software can offer a more advanced solution for recovering files after system failures. These tools scan your storage devices for lost or corrupted files and attempt to restore them.
Some popular data recovery software options include:
Recuva: This free tool is one of the most popular options for recovering lost files from damaged or corrupted drives. Recuva supports a variety of file types and can recover files from hard drives, memory cards, and USB drives.
EaseUS Data Recovery Wizard: A powerful tool that supports recovery from a wide range of devices, including hard drives, USB drives, and SD cards. It is user-friendly and has both free and premium versions, depending on the size of the data you need to recover.
Stellar Data Recovery: This tool specializes in deep scans for files that are difficult to recover. It’s particularly useful for recovering files from formatted or damaged drives, and it supports both Windows and macOS.
Disk Drill: Disk Drill is well-suited for both Windows and macOS users, offering powerful recovery features such as scanning for lost partitions, previewing recoverable files, and restoring files from encrypted devices.
To use data recovery software effectively, follow these steps:
Install the software on a different device or drive than the one you're recovering files from.
Connect the damaged device to your computer.
Run the recovery software, select the drive to scan, and initiate the scan.
Preview the recoverable files and save them to a different storage device.
While data recovery software can help recover lost files, it is most effective when dealing with logical or software failures. If your system failure involves physical hardware damage, professional recovery services may be required.
5. Professional Data Recovery Services
If the system failure is due to severe hardware damage, professional data recovery services are often the only solution. These services specialize in recovering data from damaged or malfunctioning devices, such as hard drives with physical damage (e.g., damaged read/write heads or malfunctioning motors).
Some well-known data recovery services include:
DriveSavers: A leader in data recovery, offering services for all types of devices, including hard drives, RAID arrays, and smartphones. They specialize in cases where the hardware is physically damaged.
Ontrack: Ontrack offers comprehensive data recovery services for a variety of devices and data loss situations. They also offer a “no data, no fee” policy, ensuring you don’t pay unless they successfully recover your files.
Secure Data Recovery: Known for its cleanroom facilities and cutting-edge tools, Secure Data Recovery provides data recovery from hard drives, SSDs, and RAID systems, even in extreme cases of physical failure.
These services come at a higher cost compared to DIY software options, but they offer the best chance of restoring data from severely damaged devices. They are often used as a last resort when other methods fail.
6. Prevention: Steps to Take After Data Recovery
After recovering your data, it's essential to take steps to prevent future system failures and data loss. This includes:
Regular Backups: Set up automatic backups to prevent the need for recovery in the future. Use cloud storage, external drives, or NAS solutions.
Maintain Hardware: Ensure that your devices are well-maintained. Regularly check for signs of wear and tear, and replace aging hardware components before they fail.
Use Antivirus Software: Protect your system from malware and viruses, which can corrupt files and cause system failures.
Data recovery after system failure is possible, but the best course of action depends on the nature and severity of the failure. Whether you rely on built-in recovery tools, third-party software, or professional services, the key to successful recovery lies in acting quickly and using the right methods. By following proper recovery steps and implementing preventive measures like regular backups, you can minimize the risk of future data loss and ensure that your files remain safe.
#Data Recovery#Professional Data Recovery Services#iPhone Data Recovery#Mac Data Recovery#iPad Data Recovery#Deleted File Recovery#Water-Damaged Device Data Recovery#Hard Drive Data Recovery#Data Recovery for SSDs#Encrypted Device Data Recovery#Fast and Secure Data Recovery
0 notes
Text
Discuss How Web Development Services Can Benefit Startups

Web Development for Startups: Discuss how web development services can benefit startups, from MVP development to scaling a digital presence.
Startups, often characterized by limited resources and a passion for innovation, have a unique set of challenges and opportunities. In the digital age, web development services are a vital component for startups looking to bring their vision to life and achieve growth. In this article, we’ll explore how web development services can benefit startups, from Minimum Viable Product (MVP) development to scaling a robust digital presence.
1. MVP Development: Turning Ideas into Reality
Minimum Viable Product (MVP) development is a cornerstone for startups. It involves creating a simplified version of your product with the core features that solve a specific problem or address a unique need. Web development plays a crucial role in this initial phase by:
Rapid Prototyping: Web developers can quickly create functional prototypes that allow startups to test and validate their ideas with minimal investment.
User Feedback: MVPs are an opportunity to gather valuable user feedback, enabling startups to refine and improve their product based on real-world usage.
Cost Efficiency: Developing a web-based MVP is often more cost-effective than building a complete mobile application or software platform, making it an ideal starting point for startups with limited budgets.
2. Scalability: Preparing for Growth
As startups gain traction and user demand increases, scalability becomes a critical concern. Effective web development services can help startups prepare for growth by:
Scalable Architecture: Web developers can design and implement scalable architecture that allows the platform to handle increased traffic and data without performance degradation.
Database Optimization: Proper database design and optimization are essential for ensuring that the system can grow smoothly as more users and data are added.
Load Balancing: Load balancing distributes web traffic across multiple servers, ensuring that the system remains responsive and available, even during high-demand periods.
3. Mobile Responsiveness: Reaching a Wider Audience
With mobile device usage surpassing desktops, it’s essential for startups to have a web presence that is responsive and mobile-friendly. Web development services can ensure that your website or web application:
Adapts to Different Screens: A responsive design ensures that your site functions and looks good on various devices and screen sizes, from smartphones to tablets.
Improved User Experience: Mobile-responsive websites provide a seamless and enjoyable user experience, enhancing engagement and reducing bounce rates.
Enhanced SEO: Google and other search engines prioritize mobile-responsive websites in search results, potentially boosting your startup’s visibility.
4. User-Centric Design: Building Trust and Loyalty
A user-centric design is essential for startups looking to build trust and loyalty. Web development can help in the following ways:
Intuitive User Interface (UI): A well-designed UI simplifies user interaction and navigation, making the product user-friendly.
User Experience (UX): An optimized UX ensures that users enjoy using your product, leading to increased satisfaction and loyalty.
Branding and Consistency: Web developers can create a design that reflects your brand identity and maintains consistency throughout the user journey.
5. Security and Data Protection: Safeguarding User Information
For startups, maintaining the security and privacy of user data is paramount. Web development services can ensure that your platform is secure by:
Implementing Encryption: Secure Sockets Layer (SSL) encryption and other security measures protect data transmitted between users and your server.
Data Backup and Recovery: Regular data backups and recovery procedures are vital for safeguarding information and minimizing data loss in case of unexpected events.
Authentication and Authorization: Implementing robust authentication and authorization mechanisms ensures that only authorized users can access sensitive data.
Conclusion: The Road to Startup Success
Web development is a driving force behind the success of startups. From MVP development to scalability, mobile responsiveness, user-centric design, security, and privacy, web development services provide the foundation for startups to innovate and grow. By partnering with skilled web developers and investing in their digital presence, startups can create a compelling and competitive edge in today’s dynamic business landscape.
Source:
#kushitworld#india#saharanpur#itcompany#seo#seo services#webdevelopment#digitalmarketing#websitedesigning
4 notes
·
View notes
Text
Find Lost or Missing Files on Windows 11: Quick Recovery Methods - Technology Org
New Post has been published on https://thedigitalinsider.com/find-lost-or-missing-files-on-windows-11-quick-recovery-methods-technology-org/
Find Lost or Missing Files on Windows 11: Quick Recovery Methods - Technology Org
With the advancement in technology, data loss has become a common threat in today’s digital world. You may encounter issues like sudden deletion of files and folders on your Windows 11 device. Such instances usually occur due to accidental deletion, power outages, virus or malware attacks, and many other such reasons.
Luckily, there are several tools and techniques available that you can use to find lost or missing files on Windows 11 devices. In this guide, we’ll explore effective methods to restore your precious data, focusing on the utilization of Windows data recovery software.
Why do Files Go Missing on Windows 11?
Files can go missing on Windows 11 devices due to multiple reasons, ranging from accidental deletion to software or hardware failures. Here are some prominent reasons for data loss on Windows 11:
Accidental Deletion: Human error is one of the main reasons for missing files on any device. You may have unintentionally deleted files or folders while performing other tasks on your device storage.
Formatting Errors: Formatting a drive or partition leads to the deletion of all its contents, including files and folders stored on it. To avoid such instances, you should create backup of important data stored on your drive before formatting it.
System Crashes: Sudden system crashes or power failures while performing file operations, like saving or transferring files, can cause data loss. If the file system is not properly updated before the crash, it may corrupt or lead to the deletion of files.
Malware or Virus Attacks: Malicious software, like viruses or malware, can infect your device and files stored in it. Some malware may encrypt files and demand ransom for their release, while others may simply delete or move files without any prior knowledge.
User Permissions or Settings: Sometimes, files may appear to be missing due to incorrect user permissions or settings. If you don’t have the necessary permissions to access certain files or folders, it will disappear or become inaccessible on your device.
Quick Methods to Find Lost or Missing Files on Windows 11
Now that you are familiar with the reasons for the missing files, it’s time to apply adequate recovery workarounds to find lost or missing files on Windows 11. Let’s discuss these recovery methods one by one in detail:
Method 01: Check the Recent Items Folder
If you are sure that you haven’t deleted that file from your device but it’s just not appearing where it was supposed to be, then the first place you should check is the Recent Files section. For this:
Launch This PC on your Windows 11 device. Enter the path %AppData%MicrosoftWindowsRecent in the address bar and press the Enter key to open the Recent Items folder.
Now, sort the files that appear on your screen with the Date of modification. For this, right-click on space and select Sort by > Date modified.
Scroll down to check your files according to the date. You can search for the file by typing the filename in the search box in the top right corner.
Method 02: Find Missing Files Using File History Backup
Another method to find lost or missing files on Windows 11 devices is by using the in-built File History backup utility. If you have enabled File History backup on your device, it will automatically create backup of all files stored on your device and restore them, if data loss occurs. Here’s how you can find missing files using File History:
Type File History in the search box of your desktop and click on the “Restore your files with File History” option.
Now, open the folder where your deleted file was earlier stored. You can use the left and right navigation buttons to view the different backup versions.
Select the files you need to restore and click the green Restore
Method 03: Restore Lost Files with Previous Version
Another backup alternative to find lost or missing files on Windows 11 devices is by using the Previous Version backup utility. Windows 11/10 comes with this backup option to help you back up all your important data and save it to internal or external storage devices. If you have enabled this option, follow the below steps to find disappeared missing files:
Open the folder where your lost or missing files were earlier stored.
Now, click three dots and select the Properties
Go to the Previous Versions tab, select the backup version you need to restore and click Open.
Select the files you need to restore and save them at another location on your Windows 11 device.
Method 04: Find Lost or Missing Files on Windows 11 Using Data Recovery Software
If your files are still deleted and you have no backup, you can try using a Windows data recovery software to find lost files on Windows 11. One such amazing tool is Stellar Data Recovery Standard, which supports the recovery of lost or missing files from any device in a few simple clicks. You can easily find missing files, like photos, videos, documents, etc. using this amazing tool in no time.
The software supports the recovery of files from both internal and external storage devices.
It provides an easy and user-friendly interface which allows beginners or non-tech-savvy users to find their lost or missing files.
Allows you to preview the recoverable files before saving them to your device
The software is available in multiple versions; you can check their features and select the one that best suits your requirements.
Here’s how to find lost or missing files on Windows 11 Using the Stellar Data Recovery Standard tool:
Step 1: Install Stellar Data Recovery Standard software on your Windows computer. Launch the software and from the homepage, select the type of file you need to restore and click Next.
Step 2: Now, from the Recover From window, choose the storage location where the deleted file was earlier stored and tap Scan.
Step 3: Once the scanning is completed, preview the recoverable files and choose the files you need to restore. Click the Recover button to save selected files at the desired storage location.
Conclusion
Having sudden data loss or missing files on Windows 11 can be a stressful experience, but it’s not the end of the road. With the above-mentioned methods, you can easily find lost or missing files on Windows 11 devices. Just go through the aforementioned steps and best practices and enhance your chances of successful data recovery and minimize the impact of future data loss incidents. Remember, prevention is key, so maintain regular backups and avoid saving data on your device when you encounter such issues to prevent data overwriting.
#amazing#back up#backup#backups#box#buttons#computer#crash#data#data loss#data recovery#delete#desktop#devices#easy#encrypt#Featured technology news#Features#folders#Future#green#Hardware#History#how#how to#human#impact#issues#it#malicious software
0 notes
Text
What are Cloud Solutions Management and its benefits?

Cloud Solutions Management refers to the process of overseeing and optimizing cloud-based services and resources to meet an organization's specific requirements. It involves the strategic planning, deployment, monitoring, and maintenance of cloud solutions to ensure optimal performance, security, scalability, and cost-efficiency. Cloud Solutions Management has gained significant importance in recent years as businesses increasingly leverage cloud technologies to enhance their operations and gain a competitive edge. This article explores the concept of Cloud Solutions Management and highlights its key benefits.
One of the primary benefits of Cloud Solutions Management is improved flexibility and scalability. Cloud services offer businesses the ability to scale their resources up or down based on demand, allowing them to quickly respond to changing business needs. With effective management practices in place, organizations can efficiently provision and deprovision cloud resources, ensuring that they align with current requirements. This flexibility eliminates the need for upfront investments in hardware or infrastructure and enables businesses to adapt their IT infrastructure rapidly.
Another advantage of Cloud Solutions Management is enhanced accessibility and collaboration. Cloud solutions provide a centralized platform where employees can access files, applications, and data from anywhere, at any time, using various devices. This accessibility fosters collaboration and allows teams to work seamlessly across geographies and time zones. By managing cloud solutions effectively, organizations can ensure that employees have the necessary access permissions and security measures in place to collaborate securely and boost productivity.
Cost optimization is a significant benefit of Cloud Solutions Management. By leveraging cloud-based resources, businesses can reduce their capital expenditure on hardware, software licenses, and maintenance. Instead, they can adopt a pay-as-you-go model, where they only pay for the resources they use. Effective management practices help monitor resource utilization, identify idle or underutilized resources, and optimize costs by rightsizing instances or implementing auto-scaling policies. Moreover, cloud solutions provide economies of scale, allowing organizations to benefit from the cloud provider's infrastructure and reduce operational costs.
Cloud Solutions Management also offers improved reliability and disaster recovery capabilities. Cloud service providers typically have robust data centers with redundant systems, ensuring high availability and minimizing the risk of downtime. By managing cloud solutions effectively, organizations can leverage features such as automatic backups, geo-replication, and disaster recovery plans. These features help protect critical data and applications, ensuring business continuity in the event of a failure or disaster. Regular monitoring, proactive maintenance, and system updates further contribute to the reliability of cloud solutions.
Security is a crucial aspect of Cloud Solutions Management. Cloud providers invest heavily in securing their infrastructure and implementing industry-standard security controls. However, organizations are responsible for managing access controls, data encryption, and maintaining compliance with regulatory requirements. Effective management practices involve implementing robust security measures, conducting regular security assessments, and monitoring for potential threats or vulnerabilities. With proper management, businesses can leverage the security capabilities of cloud solutions while ensuring their specific security and compliance needs are met.
Cloud Solutions Management also enables organizations to focus on their core competencies. By offloading the management and maintenance of IT infrastructure to cloud service providers, businesses can allocate their resources and expertise to areas that directly impact their growth and innovation. This shift allows IT teams to focus on strategic initiatives, application development, and delivering value-added services, rather than spending time and effort on routine infrastructure tasks.
Options with Cloud Management System
Cloud management systems (CMS) offer various options for managing and optimizing cloud resources and services. Here are some common features and options you might find in a cloud management system:
Infrastructure Management: A Cloud management systems provides tools to manage and provision cloud infrastructure resources, such as virtual machines, storage, and networking. It allows you to create, deploy, and manage these resources across different cloud providers.
Resource Monitoring and Analytics: The Cloud management systems can monitor the health, performance, and usage of your cloud resources. It provides real-time and historical data, metrics, and analytics to help you optimize resource allocation, identify bottlenecks, and troubleshoot issues.
Cost Optimization: Cloud management systems platforms often include cost management features that help you analyze and optimize your cloud spending. They provide visibility into your cloud costs, offer cost allocation and tagging capabilities, and suggest cost-saving recommendations, such as rightsizing instances or identifying idle resources.
Security and Compliance: Cloud management systems help you ensure security and compliance with industry standards and regulations. They provide features like identity and access management, encryption, security auditing, and compliance reporting to help you protect your data and meet regulatory requirements.
Automation and Orchestration: Cloud management systems platforms offer automation and orchestration capabilities, allowing you to automate repetitive tasks, streamline workflows, and define policies and rules for resource provisioning and management. This helps improve efficiency, reduce manual errors, and enforce governance across your cloud environment.
Multi-cloud and Hybrid Cloud Support: Many Cloud management systems solutions are designed to support multi-cloud and hybrid cloud environments. They provide a unified interface and management layer to control resources across different cloud providers, enabling you to leverage the benefits of multiple clouds while maintaining consistency and centralized management.
Service Catalog and Self-Service Portal: Cloud management systems platforms often include a service catalog and self-service portal that enables users to request and provision resources, such as virtual machines or databases, without manual intervention from IT teams. This empowers users while maintaining control and governance.
Backup, Disaster Recovery, and Business Continuity: Some Cloud management systems solutions offer backup, disaster recovery, and business continuity features. They provide mechanisms to automate backups, replicate data across different regions or clouds, and define recovery point objectives (RPO) and recovery time objectives (RTO) for your critical applications and data.
DevOps Integration: Cloud management systems platforms often integrate with popular DevOps tools and workflows, allowing you to seamlessly incorporate cloud management into your development and deployment processes. This integration enables activities like continuous integration, continuous deployment, and infrastructure as code (IaC).
API and Extensibility: A Cloud management systems typically provides APIs and extensibility options, allowing you to integrate it with existing systems, build custom workflows, or develop new functionalities to suit your specific requirements.
These are just some of the options and features you may find in a cloud management system. The specific capabilities and offerings may vary depending on the CMS vendor and the needs of your organization.
In conclusion, Cloud management systems plays a critical role in harnessing the full potential of cloud technologies. It offers numerous benefits, including improved flexibility, scalability, accessibility, collaboration, cost optimization, reliability, security, and the ability to focus on core competencies. Effective management practices ensure that businesses can leverage cloud solutions to drive innovation, enhance operational efficiency, and stay competitive in today's rapidly evolving digital landscape.
3 notes
·
View notes
Text
Top Data Recovery Service Provider

Data recovery simply means retrieving data that might be lost, accidentally deleted, corrupted, or left inaccessible on cloud storage platforms. The process involves setting up strategic recovery systems, backed by robust mechanisms that can restore data to the best state possible. But not only that; we can also help with cloud security and cloud management systems to ensure that your data does not become compromised in the future. While you can’t really stop natural disasters from happening, implementing a disaster recovery strategy puts you in a strong position to restore data and resume operations normally after a disaster. One of our mission is to give our customers a cost effective solution for every computer repair that they need - Data Recovery Services.
We will give you an accurate evaluation of your media to help you consider the conceivable costs and turnaround before you decide on a recovery option. Certified and secure – We put our customers’ privacy on top of everything. They employ encryption protocols, secure facilities, and strict privacy policies to protect clients’ data. Technicians sign non-disclosure agreements, ensuring that your sensitive information remains confidential throughout the recovery process. We offer expert solutions for various data loss scenarios with advanced techniques and a commitment to security - Data Recovery Company.
However, not all files stored inside are immune to data loss and may still require recovery solutions in cases of severe corruption or physical damage. To give yourself the best chance of getting your files back, it’s important to unplug your drive and stop using the device. File recovery isn’t always possible, but this combined with booking an expert data recovery service will help.
Our services include the recovery of all types of files from hard drives, such as videos, audios, images, and documents, among others. Call us to get a free consultation on hard drive data recovery from laptops, desktops, and even flash drives. A crashed hard disk often requires effort, time, and additional costs to recover files from a corrupted or lost partition. In this article, we will explore the reasons for a crashed hard drive, the potential fixes for logical errors on the HDD, and how to recover data from crashed hard drives most optimally. For more information please visit our site https://www.nowdatarecovery.com/
0 notes
Text
Essential Cybersecurity Measures for Organizational Network Protection

In today's interconnected world, a robust cybersecurity strategy is no longer a luxury, but a necessity for organizations of all sizes. A strong defense against ever-evolving cyber threats is paramount to protecting sensitive data, maintaining business continuity, and preserving reputation. This blog explores critical cybersecurity organizational network protection measures.
Understanding the Threat Landscape
Before diving into protective measures, it's crucial to understand the threats organizations face. These include:
Malware: Viruses, ransomware, and spyware designed to damage or steal data.
Phishing: Deceptive emails or messages tricking individuals into revealing sensitive information.
Denial-of-Service (DoS) Attacks: Overwhelming networks with traffic, disrupting services.
Insider Threats: Malicious or accidental actions by employees or other insiders.
Data Breaches: Unauthorized access and exfiltration of sensitive data.
Essential Cybersecurity Measures
A layered approach is key to effective network protection. Here are some crucial measures:
Firewall Implementation: Firewalls act as a barrier between your network and the outside world, controlling incoming and outgoing traffic based on predefined rules. Regularly updating firewall rules is critical.
Intrusion Detection/Prevention Systems (IDS/IPS): These systems monitor network traffic for suspicious activity, alerting administrators to potential threats and even automatically blocking malicious traffic.
Antivirus and Anti-malware Software: Deploying robust antivirus and anti-malware software on all endpoints (computers, servers, mobile devices) is essential to detect and remove malicious software. Regular updates are crucial.
Strong Password Policies and Multi-Factor Authentication (MFA): Enforcing strong, unique passwords and implementing MFA adds an extra layer of security, making it significantly harder for attackers to gain access even if a password is compromised.
Regular Security Audits and Vulnerability Assessments: Regularly assessing your network for vulnerabilities and conducting security audits helps identify weaknesses before they can be exploited.
Employee Training and Awareness: Human error is a major factor in many security breaches. Regular cybersecurity awareness training for all employees is vital. This training should cover topics like phishing awareness, password security, and safe browsing practices.
Data Encryption: Encrypting sensitive data, both in transit and at rest, protects it even if a breach occurs.
Regular Backups and Disaster Recovery Planning: Regularly backing up critical data and having a disaster recovery plan in place ensures that you can recover from a cyberattack or other disaster.
Network Segmentation: Dividing your network into smaller, isolated segments limits the impact of a breach. If one segment is compromised, the others remain protected.
Incident Response Plan: Having a well-defined incident response plan in place allows you to react quickly and effectively to a security incident, minimizing damage and downtime.
Building a Cybersecurity Culture
Effective cybersecurity is not just about technology; it's also about people and processes. Building a strong cybersecurity culture within your organization is crucial. This involves:
Leadership Buy-in: Securing support from top management is essential for allocating resources and prioritizing cybersecurity.
Open Communication: Encouraging employees to report suspicious activity without fear of reprisal.
Continuous Improvement: Regularly reviewing and updating your cybersecurity policies and procedures to stay ahead of evolving threats.
Xaltius Academy's Cybersecurity Course: Your Partner in Network Protection
Navigating the complex world of cybersecurity can be challenging. Xaltius Academy's cybersecurity course provides comprehensive training and equips you with the knowledge and skills needed to protect your organization's network. Our expert instructors and hands-on labs will prepare you to effectively implement and manage these critical security measures. Invest in your cybersecurity future and safeguard your organization's valuable assets.
Conclusion
Protecting your organization's network requires a proactive and multi-faceted approach. By implementing these essential cybersecurity measures and fostering a strong security culture, you can significantly reduce your risk of falling victim to cyberattacks and safeguard your organization's future.
1 note
·
View note
Text
Streamline Your Digital Life with Computeroids.com Backup and Driver Management Solutions
In an age where data is invaluable and hardware performance is critical, Computeroids.com emerges as a trusted platform for safeguarding your digital assets and optimizing your devices. Whether you’re a home user, a small business, or an enterprise, Computeroids.com offers cutting-edge tools for seamless backup solutions and driver management. This article dives into how their services can protect your data, enhance system stability, and keep your hardware running at its best.
Why Data Backup is Non-Negotiable
Every day, individuals and organizations face risks like ransomware attacks, hardware failures, or accidental deletions. Without a reliable backup strategy, recovering lost data can be costly—or even impossible. Computeroids.com addresses these challenges with a suite of backup solutions tailored to diverse needs.
Computeroids.com Backup Features
Smart Automated Backups:
Schedule automatic backups to local drives, network storage, or the cloud.
Customize frequency (daily, weekly, or real-time syncing) to match your workflow.
Military-Grade Security:
End-to-end encryption ensures your files remain private, even in cloud storage.
Multi-factor authentication (MFA) adds an extra layer of protection.
Hybrid Backup Flexibility:
Combine local backups for quick access with cloud storage for disaster recovery.
Ideal for businesses needing compliance with data redundancy regulations.
Version History & Point-in-Time Recovery:
Restore files from specific dates to undo accidental changes or malware damage.
Who Benefits from Computeroids.com Backups?
Home Users: Protect family photos, documents, and personal projects.
Businesses: Ensure continuity by backing up client databases, financial records, and critical apps.
Developers: Safeguard code repositories and project files with version-controlled backups.
Driver Management: The Unsung Hero of System Performance
Outdated, missing, or corrupted drivers are a common culprit behind sluggish performance, hardware malfunctions, and security vulnerabilities. Computeroids.com simplifies driver management with tools designed to keep your system running smoothly.
Computeroids.com Driver Management Tools
Automated Driver Updates:
Scan your system to detect outdated drivers and install updates with one click.
Access a vast database of verified drivers for printers, GPUs, motherboards, and more.
Driver Backup & Restore:
Create backups of current drivers before updating, allowing easy rollbacks if issues arise.
Export driver packs for quick installation on new devices or after OS reinstalls.
Compatibility Checks:
Avoid conflicts by validating driver compatibility with your OS (Windows, macOS, Linux).
Receive alerts for beta or unstable updates to prevent system instability.
Hardware Health Monitoring:
Track device performance metrics to identify driver-related bottlenecks.
Benefits of Proactive Driver Management
Faster Performance: Updated drivers unlock hardware optimizations (e.g., GPU enhancements for gaming).
Enhanced Security: Patch vulnerabilities exploited by malware.
Fewer Crashes: Resolve blue-screen errors and hardware recognition issues.
The Computeroids.com Advantage: Integration and Ease of Use
What sets Computeroids.com apart is its unified approach to system maintenance:
All-in-One Dashboard:
Manage backups, drivers, and device health from a single intuitive interface.
Ideal for users who prefer centralized control over fragmented tools.
Cross-Platform Support:
Compatible with Windows, macOS, and Linux systems.
Sync settings across devices for consistent management.
24/7 Customer Support:
Access expert assistance via live chat, email, or knowledge base tutorials.
Real-World Applications
Home Office Users: Automatically back up work files while ensuring peripherals like scanners and webcams have updated drivers.
Gamers: Keep GPU drivers current for peak gaming performance and back up saved game files to the cloud.
IT Administrators: Deploy bulk driver updates and system image backups across company devices.
Getting Started with Computeroids.com
Sign Up for Free: Start with a free tier offering basic backup storage and driver scans.
Customize Your Plan: Upgrade to premium tiers for expanded cloud storage, priority support, and advanced security features.
Automate & Forget: Set up schedules and let Computeroids.com handle the rest while you focus on productivity.
Conclusion: Future-Proof Your Digital Ecosystem
Data loss and hardware inefficiencies are preventable—not inevitable. Computeroids.com empowers users to take control of their digital environments with robust backup solutions and intelligent driver management. By combining security, automation, and user-centric design, the platform ensures your devices stay secure, fast, and reliable.
Visit Computeroids.com today to explore how their tools can transform your approach to data protection and system optimization. In the ever-evolving tech landscape, staying proactive isn’t just smart—it’s essential.
0 notes
Text
7 Best Dropbox Plugins for WordPress for 2024
Dropbox is one of the most common free cloud storage offerings. It functions very well as a secure platform for storing your WordPress backups, media files, and vital documents together. No matter the device or your location, your files are always safe with cloud storage. Dropbox let you take advantage of several benefits that can greatly amplify your website's performance, functionality, and safety.
A major reason to implement a Dropbox plugins for WordPress is the consistent approach it delivers save hosting space and manage files on cloud . The rise in the file size of your website means that the number of media files, documents, and other digital assets you have to observe increases over time. Dropbox integration for WordPress provides a feature-rich and efficient solution that improves your website experience.
Why Use Dropbox In WordPress
Dropbox WordPress Plugin allows you on your WordPress site to scale up storage capability incrementally with no need to make physical changes to your hosting. The key advantage also consist in security. Not only that, Dropbox and similar cloud storage services offer better security than traditional computers but also include encryption, secure transfer, and constant security audits for your data.
By storing files on Dropbox you contribute to relieving the pressure on the hosting server enhanced loading time and allow your web site to how in server resources for fast page downloads.
Popular plugins For Dropbox Integrations with WordPress
Integrate Dropbox
Updraft Plus
WP Media Folder
WooCommerce Dropbox
Dropr
Zapier
Out-of-the-Box
Top Reasons to Choose Integrate Dropbox over competitors
Conclusion
Integrate Dropbox free Dropbox plugins for WordPress, but we do offer premium plan in you need more advanced features from us has several compelling reasons. It offers seamless allowing users to access Dropbox files directly within the WordPress Media Library, Users can upload and download files directly from the WordPress dashboard, with automatic syncing to their Dropbox account.
Search function for Dropbox files and folders within the WordPress dashboard, enabling users to generate shortcodes for frontend display, complete with live search and thumbnail previews.
Price: Free for the base plugin, This plugin has Premium Plan
Key Features
✅ User-Specific Folders: Set up folders specific to individual users. ✅ Auto Sync/Update: Automatically (1-3 mins) sync and update new images to web pages. ✅ Media Library Integration: Seamlessly integrates with WordPress media library. ✅ Elementor Widgets: Offers custom widgets for Elementor builder. ✅ Classic & Gutenberg Editor Support: Compatible with both Classic and Block (Gutenberg) editors. ✅ Folder & File Management: Create, upload, and sync your account. ✅ Shortcode Builder: Easily generate shortcodes for custom functionality. ✅ WooCommerce Support: Works with WooCommerce for downloadable products. ✅ Slider & Carousel: Includes slider carousel for better media display. ✅ File Browser: Allows easy navigation of folders. ✅ Gallery & Media Player: Displays media in galleries and supports playback. ✅ Embed, Download, & View Links: Share using embed codes, download, and view links. ✅ File Search: Quickly search files and folders. ✅ LMS Integration: Compatible with MasterStudy LMS and Tutor LMS.
UpdraftPlus functions as a leading WordPress plugin that simplifies how to back up and restore items. Dropping in Dropbox allows users to safely and effortlessly save website backups in a cloud environment. This plugin has embodied excellence in feature delivery, especially with the functionality to make automated backup schedules that simplify recovery from any moment while also giving incremental backup options which only save modifications made since the last full backup, consequently reducing both space and resource needs. Also, UpdraftPlus guarantees that backups are encrypted before they go to Dropbox, adding an additional level of security.
Price: Free for the base plugin, This plugin has Premium Plan
https://codeconfig.dev/wp-content/uploads/2024/09/Plugin-For-WordPress-WP-Media-Folder.jpg
WP Media Folder ties your WordPress media library to Dropbox, delivering you a centralized control experience. From the WordPress dashboard, this tool provides direct means to manage and organize your Dropbox media. The user interface akin to that found on desktops makes it easy to use. The cooperation between Dropbox and WordPress reflects that all changes or updates are reachable on both platforms at each moment. With features for advanced media management such as the creation of galleries from Dropbox images, WP Media Folder serves as an efficient method for managing website media.
Price: This plugin has Premium Plan
WooCommerce Dropbox
WooCommerce Dropbox brings a way for store owners to connect their digital goods to files already in Dropbox. WooCommerce Dropbox serves to increase the capabilities and usefulness of the e-commerce platform besides ensuring the customers get their products, especially the digital ones, on easily and on time. This setup really helps those selling digital items like software music or videos.
Shoppers get fast and simple downloads without slowing the website down. Using less server effort helps the site stay strong when many people visit. WooCommerce Dropbox plugin changes the usability of downloadable products as it is connected with Dropbox storage answers. This integration enables the e-commerce site owners to be able to host their downloadable content on Dropbox so that they can conserved server space and make their customers gain faster access to their downloads.
Price: Free for the base plugin
Dropr makes it straightforward to connect Dropbox with your WordPress site. By setting Dropbox as the primary storage for media files, it ensures that all uploads are directly stored in Dropbox, thus freeing up local storage space on the server. Dropr is the cool solution to share Dropbox files as your WordPress media library and embed them in your posts. When it comes to uploading images, videos or documents to your site using Dropr is as easy as working with local files.
This integration proves to be the most advantageous for sites containing a lot of posts and other resources, that would need constant updates and availability of different types of media. With help of Dropr ordinary file transfers take less time and you are able to deliver fresh and active contents for your site all the time.
Price: Free for the base plugin, This plugin has Premium Plan

Zapier get expanded by WordPress and Dropbox to perform processes connecting the two applications. While they are not regularly considered as plugins, Zapier can interconnect these platforms and create complex automated workflows which can then increase efficiency and cooperation. For example, when you need the content to be posted on your WordPress site and files are included in the Dropbox, one can set a Zap to accomplish this duty. It is especially helpful for teams that can get overwhelmed when they need a constantly updated and efficient web-based operations dashboard.
Price: Free for the base plugin, This plugin has Premium Plan

Out of the box provides a new way of handling Dropbox files by integrating it within the WordPress environment. Its integrates your Dropbox media into your WordPress Website and dragging and dropping of the contents into your content is possible in real time. Its allowing for a seamless user interface when dealing with content on WordPress platforms.
Price: This plugin has Premium Plan
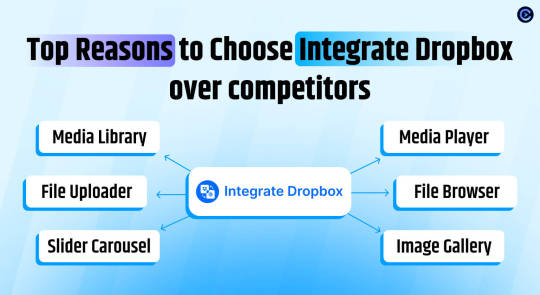
Integrate Dropbox Free dropbox plugins for WordPress makes it easy to link your WordPress site to the Dropbox account and it is the best tool when it comes to organizing files. These are particularly useful to site owners with frequently updating content on the web and requires a single platform to manage it. This way, Integrate Dropbox helps users avoid numerous difficulties connected with files synchronization and access with the help of WordPress dashboard only.
The File Browser provides a web-based interface for convenient access and management of Dropbox files from any device. The Media Player allows users to play Dropbox media files using a customizable player on WordPress site. Users can easily create and name unlimited shortcodes When buy premium for integrating content anywhere on the website, compatible with popular themes.
These features collectively enhance usability, integration, and media management, making the "Integrate Dropbox" plugin a strong choice for WordPress users.
🧩 RICH INTEGRATION WITH POPULAR PLUGINS
▶️ Media Library Integration Simply use your Dropbox files from WordPress Media library and add the images in pages and posts as media, featured images, galleries, etc. Get the Image from Dropbox directly.
🔀 Gutenberg Block Editor Integration Integrate Dropbox allows 7 blocks for using File Browser, Gallery, Media Player, Slider, View, and Download link modules in the Gutenberg editor.
🔀 Elementor Website Builder Integration This plugin integrates with Elementor, offering over 7 widgets for File Browser, Gallery, Media Player, Slider, View, and Download link modules.
Conclusion
Integration of Dropbox on WordPress has turned into a necessary technique for current website administration. These successful tools deliver an effective solution for increasing file organization, improving backup processes, and supporting smooth collaboration. Using plugins developed to link with Dropbox, integrate dropbox, or WP Media Folder, website administrators and content developers can remarkably accelerate their workflow efficiency and digital media management.
Eventually, having the right Dropbox WordPress Plugin may change the way users control their WordPress website, both saving server space and increasing website performance. Hosting and putting into action these integration tools enables WordPress users to establish a more productive online workspace, securing their content and making it ready for effortless deployment across their various online platforms.
0 notes